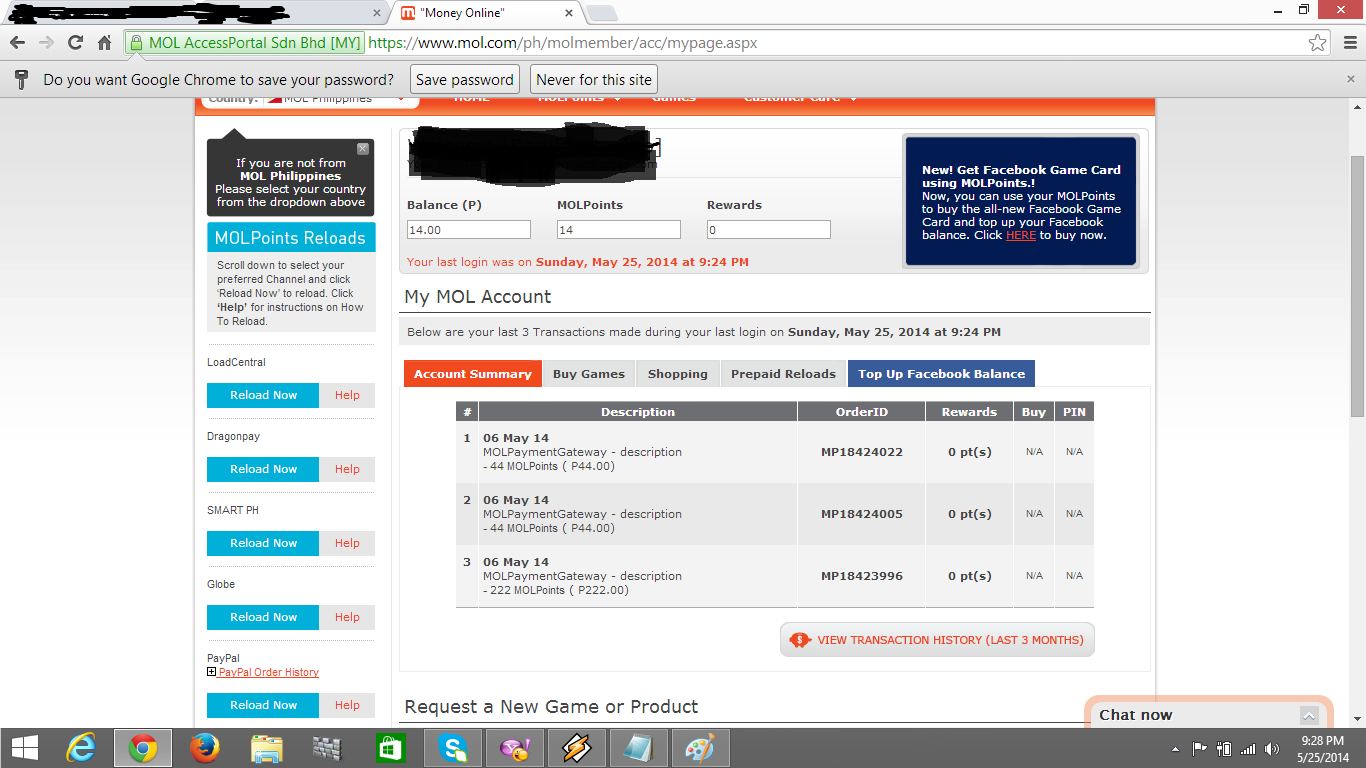
Dan masukkan pin number/serial number yang ada kat kertas mol korg tu. And write your serial number and pin no. / Now you all can see your mol point.
Anti-Detection We use private proxies and everything is done on our server to ensure hack is not detected. Free Mol Points Serial Number & Pin Generator Hack Server: Online Spyware, Adware As Well As Various Other Harmful Software applications There are 2 distinctive kinds of destructive software application, one is the adware as well as the various other one is the Spyware. On the various other hand destructive software application like spyware as well as adware are individually configured applications and also does not require the aid of a page to cause its impacts. Spywares do not truly impact your computer system right away, unlike an infection where computer systems have the radical and also virtually instantaneous results Spywares simply rest inside your computer system opening up web links to as well as advertisement or routing you to it. One point you'll see is that the spyware is frequently obtaining in the means of your company and also the spyware is quite difficult to find since it does not consist of the common shows string regular infections have. From the cars and trucks we own to the net that we make use of.
Due to the fact that of the consistent climb of the net and also details innovation in the direction of much better as well as much more hassle-free methods of mass moving of information, pictures, sound and also video clip documents as well as practically transferable as well as portable item of info over a network, individuals have actually additionally discovered countless means of maintaining up with the considerably altering network atmosphere. With all the innovation existing as well as all set for use anytime, anywhere, the number of harmful software applications like spyware, that are not always infections however positions the very same degree of danger if left to be tested and also untreated, have actually likewise expanded to triple their previous dimension and also maintains on expanding. Destructive software applications are the kinds of software applications that instantly turn on a web link while we are on the web.
There are 2 unique kinds of harmful software program, one is the adware and also the various other one is the Spyware. A pop-up advertisement nonetheless simply stands out up at arbitrary throughout any type of event that we are making use of the net. Developers have actually created a means to put a pop-up advertisement right into the shows string of a web page. On the various other hand harmful software application like spyware as well as adware are individually set applications as well as does not require the aid of a website to activate its impacts. Spywares do not actually impact your computer system right away, unlike an infection where computer systems have the radical as well as virtually immediate impacts Spywares simply rest inside your computer system opening up web links to and also advertisement or guiding you to it.
One point you'll observe is that the spyware is regularly obtaining in the means of your service as well as the spyware is very difficult to spot due to the fact that it does not have the typical programs string regular infections have. Spywares obtain handed down to our computer system basically unseen, yet software program suppliers have actually developed a method of resolving our spyware issues for us. They have actually developed a spyware discovery software program that checks the computer system for programs codes that would typically have a great deal of links.
Spywares are truly a hazard to us and also our computer systems yet with the ideal details and also the correct devices we could shield our financial investment from spyware, adware as well as anything else they could think of. Find out Ways To Avoid Identification Burglary All you have to do is to avoid on your own from being the target. Exactly how are you going to do that? The most effective method to secure you from being a sufferer of identification burglary is to shield your info. You must understand all the opportunities that your details could be gotten. You should be of excellent control over your details to prevent it from being taken.
No person wishes to be a target of identification burglary, as it is so hard to remove all the purchase made by these burglars. If you do not have sufficient understanding regarding it, you will certainly not be stopped from being a sufferer of it. Review this short article and also learn exactly how you could avoid being taken advantage of by these burglars. You need to understand the methods to get your details.
There remain in truth several methods to obtain it. These are the adhering to methods: - Acquiring items as well as solutions over the web - Electronic banking - Getting rid of your previous charge card without damaging it - Saving individual information as well as details in your computer system - Mobile phone usage - Wireless phone usage - Utilizing your passwords and also numbers for recognition You should guard your individual info utilizing the complying with strategies. You need to be aware regarding it, as it will certainly offer you correct education and learning on just what to do and also just what to find out in regards to managing your account. Adhere to these basic standards to safeguard on your own from the injury of identification burglary: - Don't bother the mails that inform you to finish your application on charge card specifically on the internet. - Need your credit scores bureaus to provide you routine records on the testimonial of your charge account.
- Offer your data security from making passwords. These could just be opened up if your individual safety and security code or password is gotten in.
Never ever utilize your birth day or your name as a password; it could be a very easy hunch to individuals. - Never ever open mail accessories if you are not certain concerning that sent it to you. This issue could be resolved by making use of software application that obtains rid of them.
- Do not supply individual details when you are filling out types on-line. Do not supply your individual information as well as a lot of unique your economic info online. - If you shed your bank card of various other crucial cards report regarding it promptly to accredited workers. You need to momentarily shut your account up until the card has actually been caught.
You ought to be mindful of the methods to get your details. You require to guard your individual info making use of the adhering to strategies.
- Never ever open mail add-ons if you are not certain regarding that sent it to you. - Mount software program in your computer system to prevent harmful software application to enter your computer system. Software program such as firewall software will certainly decrease the possibilities of downloading and install poor software program such as spyware, adware, as well as keyloggers. - It is more secure to remember your protection codes and also numbers besides composing it down. Never ever publish these numbers on your checks.
- Never ever throw out financial institution invoices, charge card invoices as well as deal invoice in public locations. Some individuals could get this info as well as utilize it versus you. These are the standards to safeguard you from experiencing the rage of identification burglary.
Make certain to comply with these standards well for the defense of you accounts. You could offer your economic details as well as various other information if you are the one to start the discussion.
- Damage all the papers which contain your individual information and also details. Burning them could be much more better. - Throughout a phone call, never ever offer your individual information and also info on the one you are speaking to.
- Never ever throw out any type of formerly made use of charge card prior to damaging it. Shred it splits it and also torn it right into items to safeguard that these charge card will certainly not be utilized once more. - Do not include your individual details on the e-mail questions. You must additionally stay clear of sending out details over e-mail.
This software application will unnoticeably enter your computer system to snoop on all the procedure made in your computer system. With using firewall programs, you make certain to obtain eliminate this harmful software program in genuine time. The ideal method to secure you from being a target of identification burglary is to shield your info. Anjunadeep Edition 235 With James Grant Tracklist The Life.
You need to be of great control over your details to prevent it from being taken. If you make sure that the respectable site sent you a company deal, most likely to the authorities internet site of the sender to respond. Never ever utilize the web link showed on the e-mail sent out.,,,,,,,,,, .
If you were looking for a working MOL-Free Points then you came to the right place because MOL Points G enerator is finally out in the market and game lovers can’t wait to have the hack in use..This MOL Points Generator Hack is easy, based on few steps, all you have to do is download it and click hack to get started. With this hack you will be able to generate as much points as you want without being caught and noticed! The ways of downloading the hack will be highlighted below here but after understanding deeply what MOL is. What are MOL Points? Well, this is an online payment system that allows users to purchase games, products & services and other online games goodies. The system has been developed by MOL-AccessPortal Sdn.
Reward points allows players to enjoy convenience of getting games and all their goodies without having to struggle much. How about getting the points for free? Yea, it sounds interesting to game lovers. We are glad to announce that the new hack that has been released is capable of earning free points to users. Nokia 5233 Water Themes Free Download. MOL Points Generator Features: Works PERFECT Globally-No matter where you stay – US,UK,CA or Anywhere in the world. You WILL NOT get banned for using this (100% guarantee) Works on ALL internet browsers (Firefox.Chrome,Safari,Operaetc) Tested on daily basis to ensure it’s functionality.
If the hack is patched, UPDATE will be done within 12 hours. (100% Satisfaction) Easy to use. Simply click hack and you are done. The MOST stable hack ever created on net – Run as many times as you wish without a single error.
The ONLY WORKING and LEGIT Mol Points Hack Generator on the net. (100% Satisfaction).
Rated Number 1# hack in terms of speed and efficiency (100% guarantee) 24/7 ONLINE server – you will not get any error connecting to our database while using this hack (100% guarantee) Instructions MOL Points Generator: 1.Download MOL Points Generator.rar and use the details provided in the Readme.txt 2.Open it. Select the amount you want to generate 3.Enter your email address 4.Hit Generate, make sure there is a green check mark.
The green check mark shows that the confirmation has been checked with the MOL servers to see if it is unused. 5.If you want you can share with your friends through social networks,that will help us a lot.Thank you!
VIRUS SCAN: MOL Points Generator was succesfully scanned.